Data Governance#
The Neoflow ecosystem depends on industry and government stakeholders working together to enable the creation of a digital representation of an asset complete with lifecycle events and attributes. In this way, a viable ecosystem necessitates value chain participants who are actively part of the business workflow, read, write and commit data to the platform. These participants may run their own nodes or may have their nodes operated by Neoflow. In addition, there will be value chain ecosystem users who leverage data for the purposes of regulation, value chain monitoring or to gain market intelligence.
The table below outlines the different network participants, their roles and permissions within the system, as well as examples of their function in the Oil & Gas value chain.
| System Roles | Permissions | Role within the Oil & Gas Value Chain | |
|---|---|---|---|
| Value Chain Participants | Data providers, owners and users (node operators) | Read, write and commit transactions on the system | Oil & Gas producer, shipper, pipeline, custom broker, etc. |
| Value Chain Ecosystem | Data users | Access the system and see transactions for the purposes of monitoring | U.S. Customs and Border Protection (CBP) |
| Technology providers | Infrastructure and applications development, IT support and additional services | No read, write or transaction issuing permissions. Only access to sample data to enhance or roll out new features with data holders’ consent. No permission to share beyond consolidated industry reports and anomaly detection. | Third party service providers |
Data Visibility#
To provide user with transparency on product lifecycle and business data, as well as ability to automate order, contract and digital border clearance, Neoflow stores five types of data. The diagram below illustrates the different layers of data and the respective access restrictions within the ecosystem. It is important to note that protected data never travels to other parties unless explicitly shared and public data is public only within Neoflow.
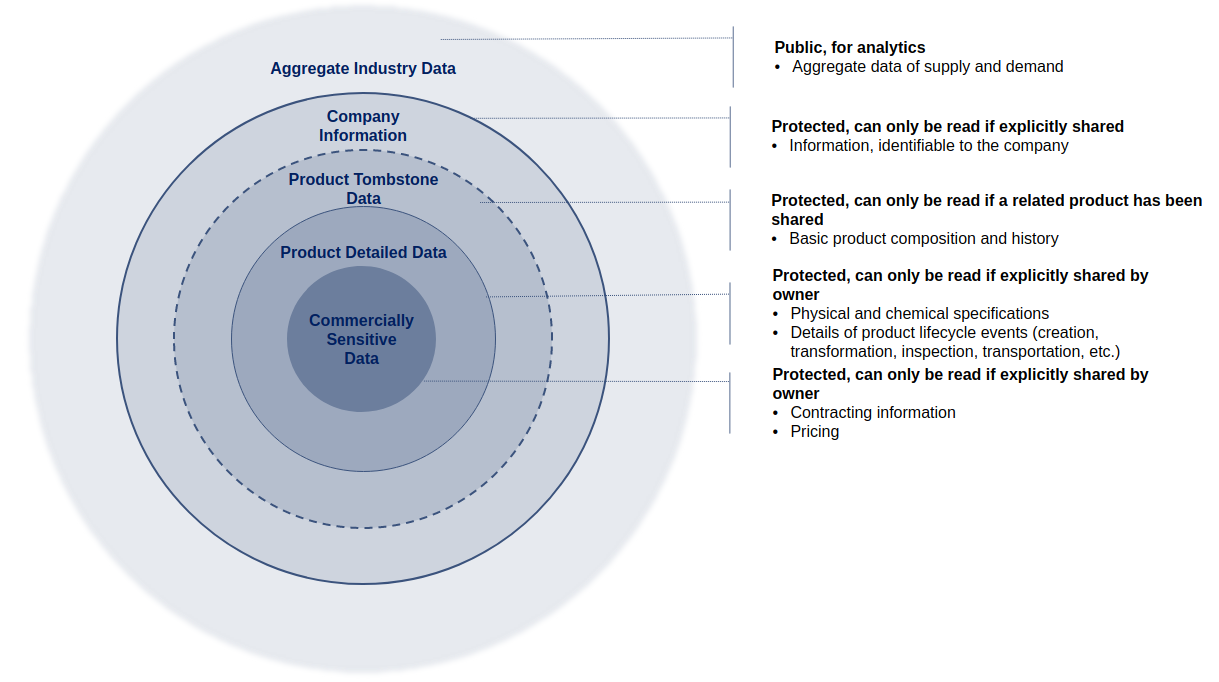
For the purposes of illustration, we have included some examples of the types of data that would fall under each bucket in the table below.
| Data Types | Description | Accessibility | Examples |
|---|---|---|---|
| Product Tombstone Data | Used for visualizing complete product lifecycle | Protected |
|
| Product Detailed Data | Used for visualizing complete product lifecycle in details. Contains product sensitive data | Protected |
|
| Commercially Sensitive Data | Used for automating order, contract and border clearance. Contains commercially sensitive data | Private |
|
| Company Info | Used for automating order, contract and border clearance | Protected |
|
| Aggregate Data | Used for data analytics and value chain insights | Public within Neoflow |
|
Data Sharing and Accessibility#
For each network participants, Neoflow enforces strict rules listed in the below table for data privacy and accessibility. Neoflow also ensures that all Product Detailed Data owners can see which network participant holds a Degree-2 accessibility, and can grant and revoke the access at all times.
| Network Participants | Data Type | Permission | |||
|---|---|---|---|---|---|
| Read if a related product has been shared (Degree-1) |
Read if the owner grants access explicitly (Degree-2) |
Can only read owned data (Degree-3) |
Read and download (Degree-4) |
||
| Value Chain Stakeholders | Product Tombstone Data | ✅ | |||
| Product Detailed Data | ✅ | ||||
| Commercially Sensitive | ✅ | ||||
| Company Info | ✅ | ||||
| Aggregated Data | ✅ | ||||
| Value Chain Ecosystem | Product Tombstone Data | ✅ | |||
| Product Detailed Data | ✅ | ||||
| Commercially Sensitive | ✅ | ||||
| Aggregated Data | ✅ | ||||
| Technology Providers | Product Tombstone Data | Permitted to collect and use the data samples to support Neoflow features; NOT Permitted to share with 3rd parties beyond consolidated industry reports and anomaly detection |
|||
| Product Detailed Data | |||||
| Commercially Sensitive | |||||
| Company Info | |||||
| Aggregated Data | |||||